
Maritime systems' exploitation research and RF penetesting
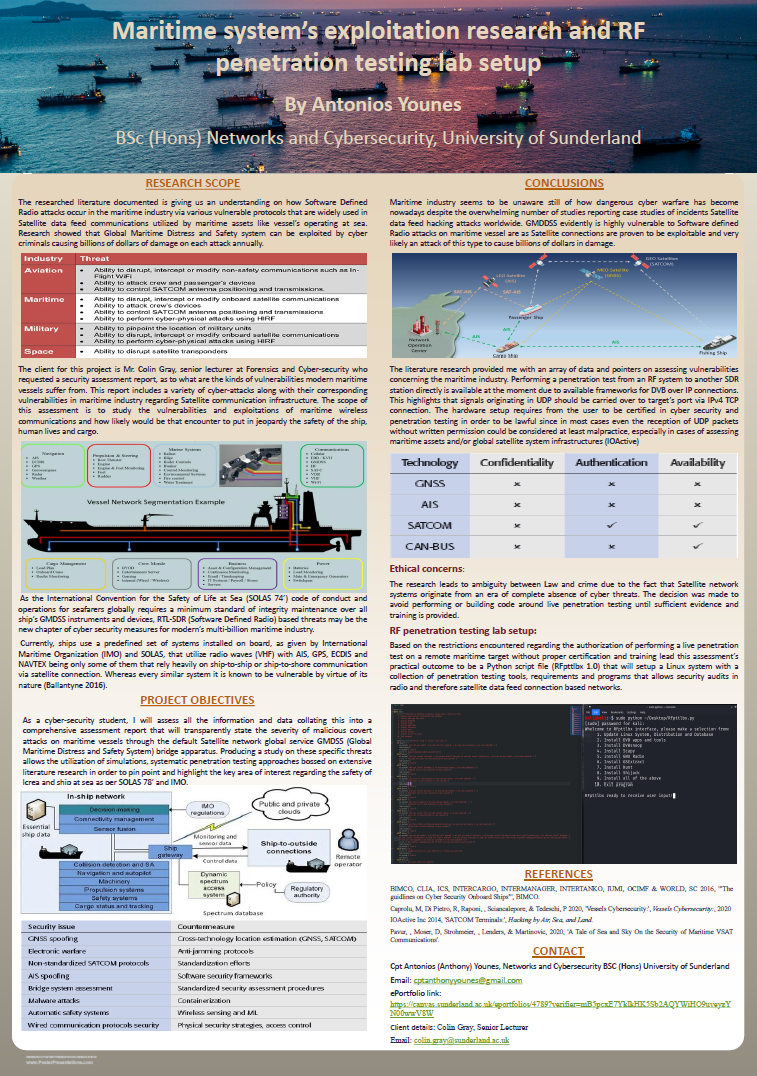
Company: Merchant Marine Service
Core Theme:
Investigation of maritime cyber-security vulnerabilities in shipboard satellite communications, focusing on RF (Radio Frequency) and SDR (Software Defined Radio) attack surfaces in critical maritime systems (GMDSS, AIS, ECDIS, GNSS, VSAT, CAN-BUS, etc).
Objective:
To identify exploitable weaknesses in maritime satellite data feeds, assess the real-world risk of SDR-based attacks, and design a safe, ethical RF penetration testing lab environment using open-source SDR tools.
Practical Outcome:
A passive Python script for Kali Linux that prepares a penetration tester’s system with cutting-edge SDR tools (DVBSnoop, Scapy, GNU Radio, GSExtract, Hunt, Shijack, Juggernaut), alongside a hardware setup report and recommendations for legal/ethical penetration testing.
By Antonios Younes – BSc Networks and Cybersecurity, University of Sunderland
Research Focus
Investigation of maritime cyber-security vulnerabilities in shipboard satellite communications, focusing on RF (Radio Frequency) and SDR (Software Defined Radio) attack surfaces in critical maritime systems (GMDSS, AIS, ECDIS, GNSS, VSAT, CAN-BUS, etc).
To identify exploitable weaknesses in maritime satellite data feeds, assess the real-world risk of SDR-based attacks, and design a safe, ethical RF penetration testing lab environment using open-source SDR tools.
A passive Python script for Kali Linux that prepares a penetration tester’s system with cutting-edge SDR tools (DVBSnoop, Scapy, GNU Radio, GSExtract, Hunt, Shijack, Juggernaut), alongside a hardware setup report and recommendations for legal/ethical penetration testing.
Key Research Elements
Problem Context
- Maritime vessels depend heavily on satellite-based, radio-linked systems—many of which were not designed with cybersecurity in mind.
- Attackers can exploit unauthenticated, unencrypted radio protocols (DVB, GSE, AIS, GNSS) to:
- Spoof navigation
- Jam emergency comms
- Hijack system controls
- Disrupt SAR operations
- Cause financial losses (potentially billions)
Methodology
- Adaptive Software Development (ASD):
Chosen for its flexibility over rigid waterfall, suitable given legal/ethical constraints and fast-evolving threat landscape. - Approach:
Comprehensive literature review, systems analysis, requirements gathering, prototype (Python script + lab), evaluation. -
Technical Research
- Vulnerabilities Explored:
- GMDSS, AIS, GNSS, ECDIS, VSAT, CAN-BUS—focus on protocol and hardware weaknesses (e.g., lack of authentication, outdated software, vulnerable update processes).
- Examples: GPS spoofing, AIS data injection, satellite link hijacking, malware on ECDIS, CAN-BUS command injection.
- Toolbox:
- DVBSnoop: Satellite stream analyser
- Scapy: Wireless packet crafting/fuzzing
- GNU Radio: SDR app development and simulation
- GSExtract: VSAT IP packet extraction
- Hunt, Shijack, Juggernaut: Session hijacking and traffic manipulation tools
- Lab Setup
- Hardware: Linux machine, DVB-S2 PCI card (TBS6903), SelfSat Flat antenna, LNA, coaxial cables.
- Software: Python, Kali Linux, suite of SDR tools.
Ethical & Legal Framework
- Passive-only design:
No live attacks performed; all active exploit code or “dangerous” payloads omitted. - Justification:
Maritime and satellite networks are critical infrastructure; live attacks are illegal without explicit permission.
Conclusions
- Main Findings:
The maritime industry is alarmingly exposed to SDR/RF attacks due to legacy protocols, slow adoption of cyber-hygiene, and regulatory gaps. - Impact:
Attacks can endanger lives, disrupt global trade, and result in catastrophic financial and reputational damage. - Recommendations:
- Urgent overhaul of maritime satellite security standards.
- Mandatory training for GMDSS operators on RF/cyber threats.
- Further research into robust, authenticated protocols and system hardening.
Dissertation Structure (Summary Table)
| Chapter / Section | Key Topics |
|---|---|
| Introduction | Problem context, objectives |
| Literature Review | Maritime protocols, SDR, cyber-attack scenarios |
| Intelligence Gathering | Requirements, legal/ethical assessment |
| Design | Lab setup, toolchain, system architecture |
| Development & Testing | Script/lab implementation, test results |
| Evaluation | Self, process, artefact review |
| Conclusions & Recommendations | Findings, limitations, future directions |
| Appendices | Diagrams, proposals, specs, bibliography |